Strandhogg, a term that could sound new to many, is a cybersecurity vulnerability that has unobtrusively represented a huge threat to the digital world. In this comprehensive blog post, we will dig profound into the world of Strandhogg, investigating its complexities, expected dangers, and the actions that can be taken to shield against it. Thus, attach your digital safety belts as we set out on this excursion to figure out the intricate details of this threatening vulnerability.
Source: bleepingcomputer.com
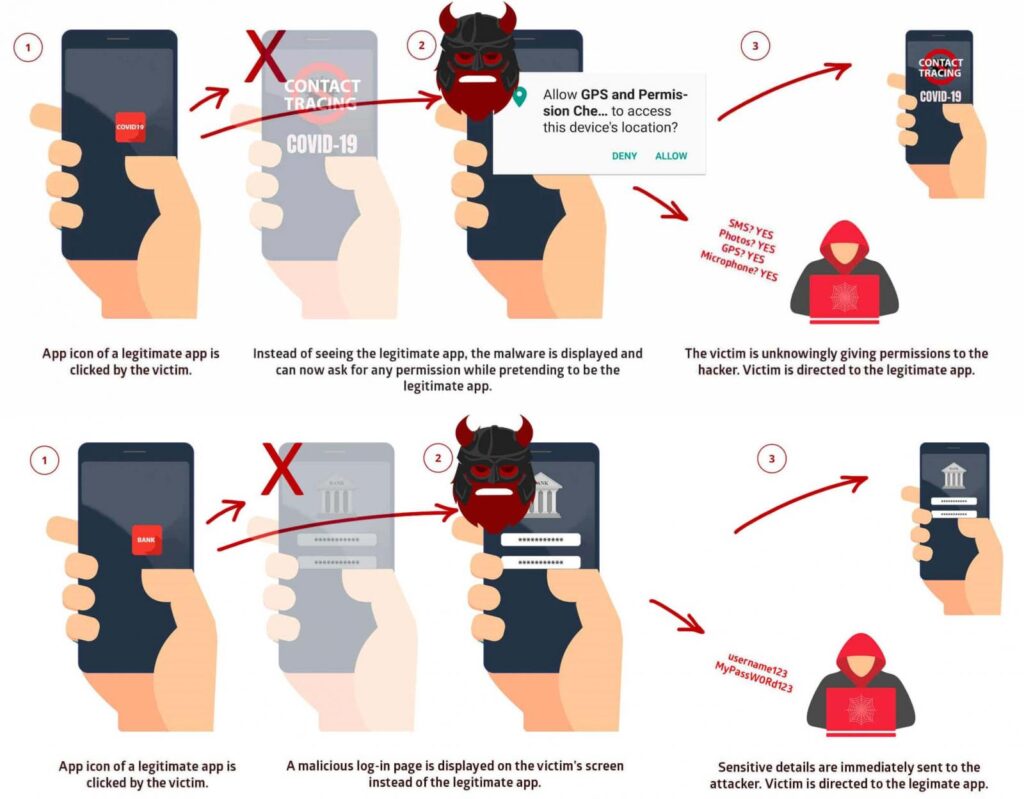
- The Anatomy of Strandhogg: To understand the gravity of Strandhogg’s risk, it’s essential to initially take apart its anatomy. At its center, Strandhogg is an Android vulnerability that exploits the multitasking element of Android gadgets. It permits malicious apps to act like genuine ones, basically “hijacking” the user interface (UI) and granting access to sensitive user data.
- The Art of Deception: One of the most agitating parts of Strandhogg is its capacity to trick users. It can make persuading overlays regarding trusted apps, for example, banking or social media apps, making it almost incomprehensible for users to recognize the certified and the malicious. This deception makes it so risky, as users accidentally enter their credentials and sensitive data into these phony interfaces.
- The Scope of the Threat: The risk of Strandhogg stretches out a long way past taking login credentials. When an attacker gets entrance, they can control many functionalities on the casualty’s gadget. This incorporates accessing photographs, messages, call logs, and in any event, listening in on discussions through the gadget’s mouthpiece. The broadness of potential harm is faltering.
- The Real-World Impact: Real-world cases of Strandhogg’s double-dealing have been accounted for, featuring the seriousness of the threat. Attackers have utilized this vulnerability to perpetrate different types of cybercrime, including data fraud, monetary misrepresentation, and surveillance. The implications for people and associations are disturbing.
- The Challenge of Detection: Identifying Strandhogg can be astoundingly tested because of its capacity to mirror real apps consistently. Customary antivirus and security measures may not do the trick, making it basic for users and associations to embrace progressed threat detection strategies.
- Mitigation and Protection: Moderating the dangers presented by Strandhogg implies a diverse approach. Users ought to practice alert while downloading apps and just utilize confided-in sources, for example, official app stores. Routinely refreshing the Android working framework and apps is significant, as security patches are often delivered to address weaknesses like Strandhogg.
- Stay Informed and Vigilant: Mindfulness is a powerful device in the battle against Strandhogg. Users ought to instruct themselves about this vulnerability and its possible risks. Being vigilant and careful while communicating with apps and granting permissions can go far in forestalling an attack.
- Targeting the Heart of Android: What makes Strandhogg particularly hazardous is its capacity to take advantage of Android’s center elements. It doesn’t depend on unpredictable specialized imperfections but instead uses the intrinsic plan of Android’s multitasking framework. This implies that even all around kept up with and refreshed Android gadgets are defenseless to this vulnerability.
- Third-Party App Risks: While official app stores have thorough screening processes set up to limit the gamble of malicious apps, the risk of Strandhogg often emerges from apps obtained from third-party sources. These unsubstantiated sources can hold onto malicious forms of famous apps, making users who download from them more helpless against abuse. A good way to be safe from these types of threats is to consult with experts from organizations like Appsealing.
- Expanding Attack Vectors: Over the long haul, cybercriminals have advanced Strandhogg to target different ventures and people. From monetary organizations to medical care suppliers and government offices, no area is insusceptible. Besides, not just individual users are in danger; even ventures can succumb to Strandhogg attacks, possibly prompting data breaks and monetary misfortunes.
- Social Engineering Tactics: In the realm of cybersecurity, social engineering tactics play a vital part. Strandhogg profits from this by fooling users into uncovering sensitive data or granting superfluous permissions. For instance, an overlay can provoke a user to enter their PIN or biometric data, which is then caught by the attacker.
- Cross-Platform Threat: While at first recognized as an Android vulnerability, Strandhogg’s risk isn’t restricted to a solitary platform. Cybercriminals are constantly attempting to adjust and convey comparable attacks on other working frameworks, including iOS. This cross-platform threat highlights the requirement for a comprehensive and versatile cybersecurity system.
- Legal and Ethical Implications: Past its specialized viewpoints, Strandhogg raises ethical and legal worries. The abuse of individual data and the split of the difference in user security can prompt huge legal repercussions for attackers whenever they are caught. Understanding the legal outcomes of such cybercrimes is essential in the battle against Strandhogg.
- Ongoing Security Research: The fight against Strandhogg is ongoing. Security researchers, alongside tech organizations, are continually concentrating on vulnerability to foster more strong guards. Staying informed about the most recent improvements in the field is crucial for people and associations trying to successfully safeguard themselves.
- Evasion of Permission Requests: One of the disturbing parts of Strandhogg is its capacity to sidestep Android’s permission framework. In any event, when an app requests specific permissions upon establishment, Strandhogg can access these elements without express user assent. This makes it provoking for users to depend entirely on permissions as a security boundary.
- Credential Harvesting and Phishing: In the possession of cybercriminals, Strandhogg can be utilized for credential harvesting and phishing attacks for an enormous scope. Attackers can overlay counterfeit login evaluations for famous apps, gathering usernames and passwords that can later be utilized for unapproved access to different web-based accounts.

Source: komando.com
Conclusion: In conclusion, the Strandhogg vulnerability addresses a strong and ever-present risk in the digital scene. Its capacity to hoodwink users, compromise data, and unleash destruction on Android gadgets makes it an imposing foe. To safeguard oneself from this danger, a mix of user watchfulness, ordinary updates, and high-level threat detection is fundamental. As innovation keeps on progressing, so too will the tactics of cybercriminals. It falls upon us, the users, to stay informed and go to proactive lengths to shield against threats like Strandhogg in our consistently associated world.



